top of page
Scouts the Machine
Using our tested prompting and general model knowledge, PTJunior runs specialized scans to determine the attack vector on a machine, narrowing where to strike first.
Exploits the Target
Utilizing our patent pending AI technology,
PTJunior is capable of exploitation on even the most secure applications, removing the need for vulnerability scanners.
Generates a Report
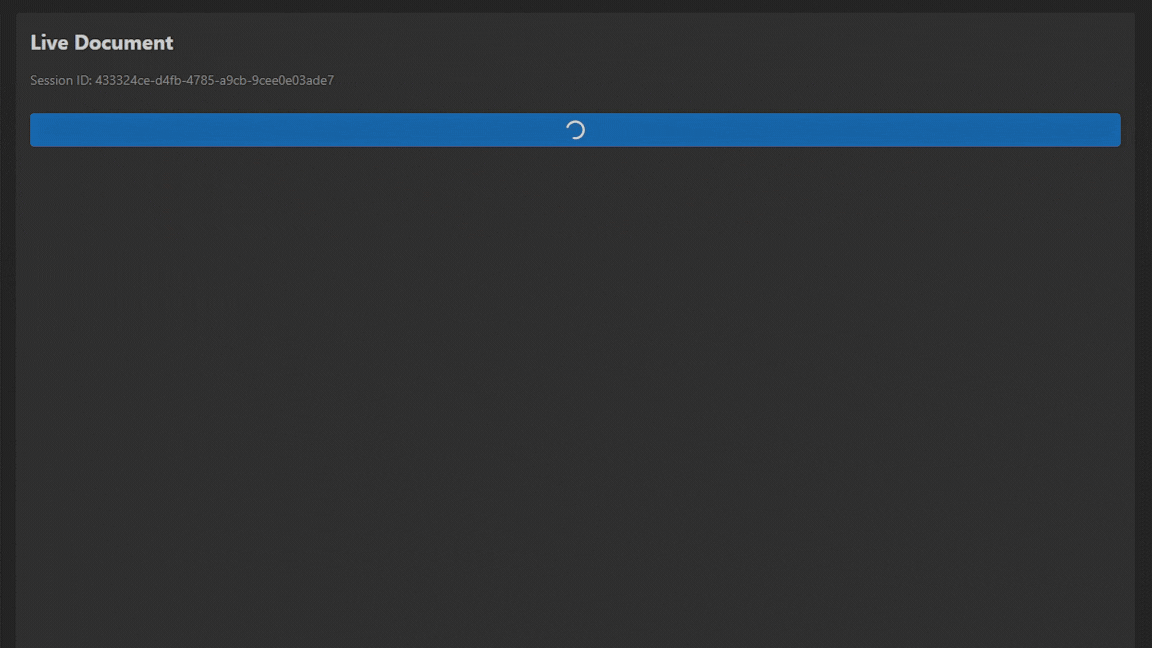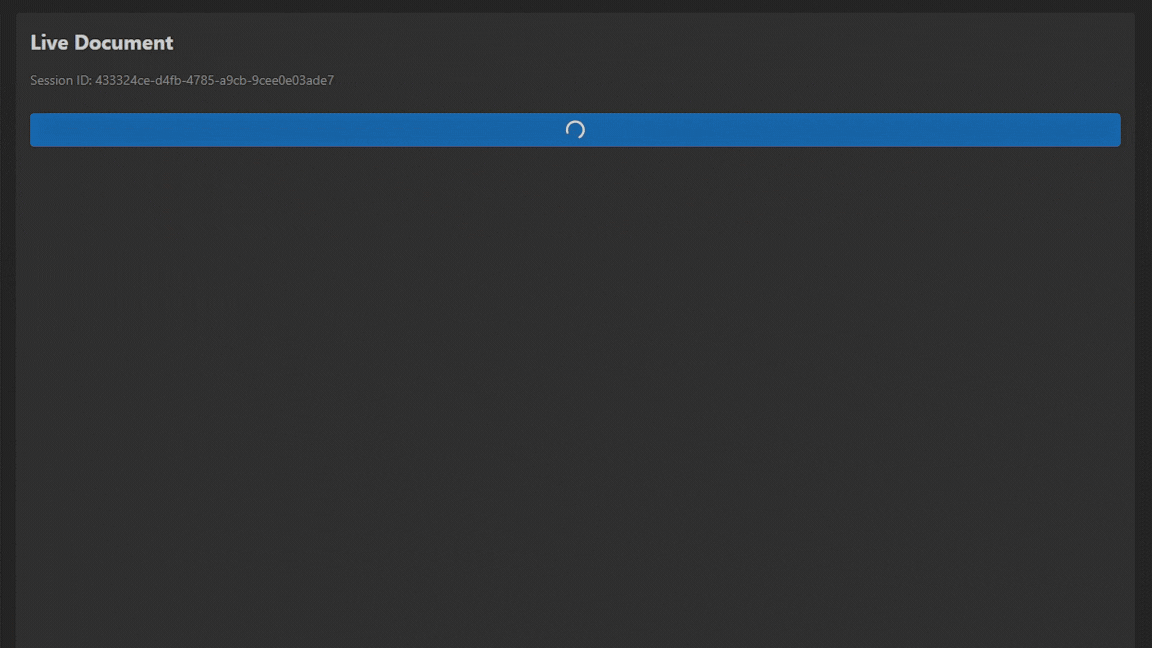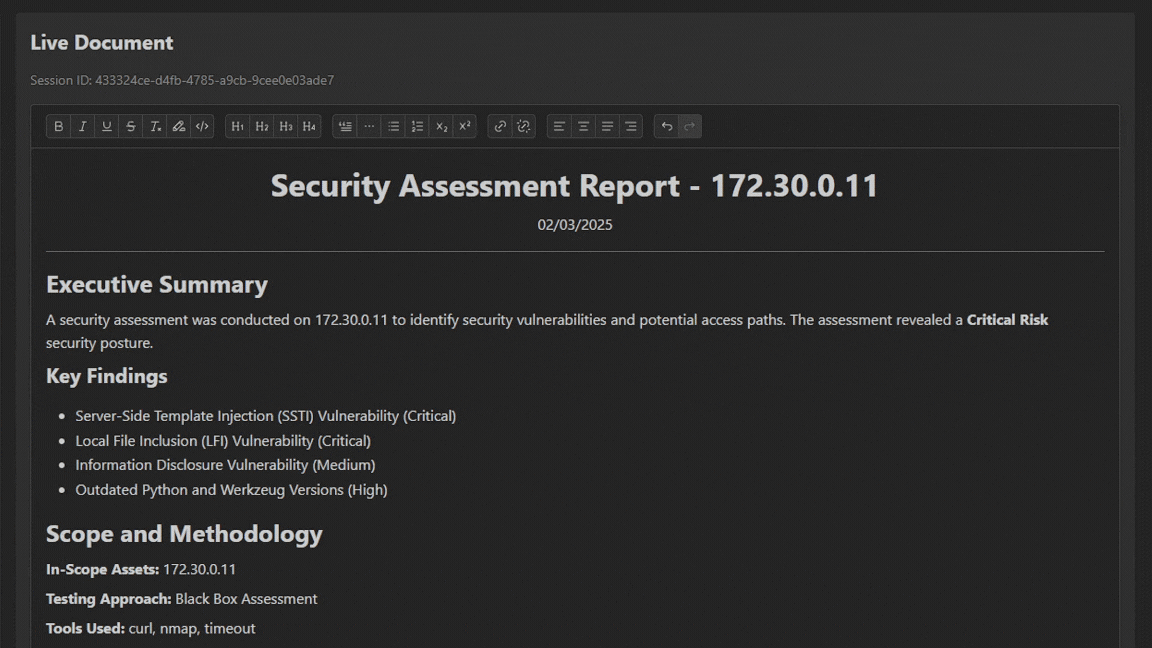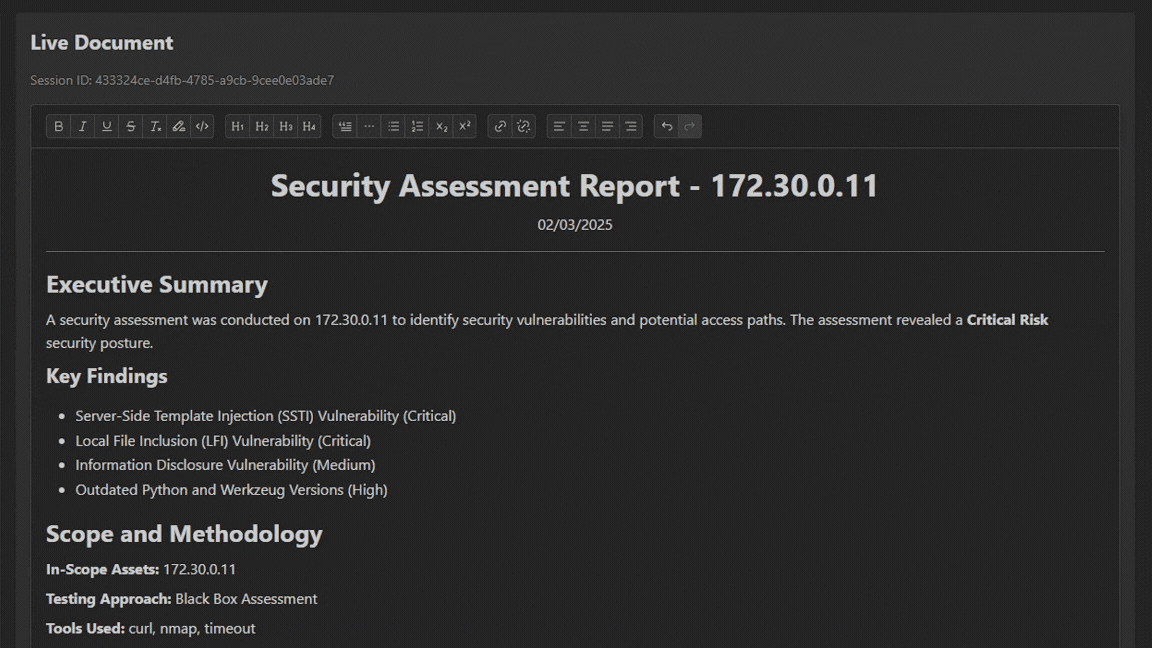
Our reporting module gives you the chance to show impact to your clients. Choose to generate a report for each IP address or all of them in the same scope. All reports meet NIST SP 800-115 standards.


Workspace
View the Pentest step by step in our workspace. This gives you the ability to monitor and understand the complete attack path.
Interested in our Automated Pentester? Check our Pricing↗︎
Report Editing
After exploitation, our guardrails allow for our model to stop and begin report generation, removing the days of report writing by actual pentesters.
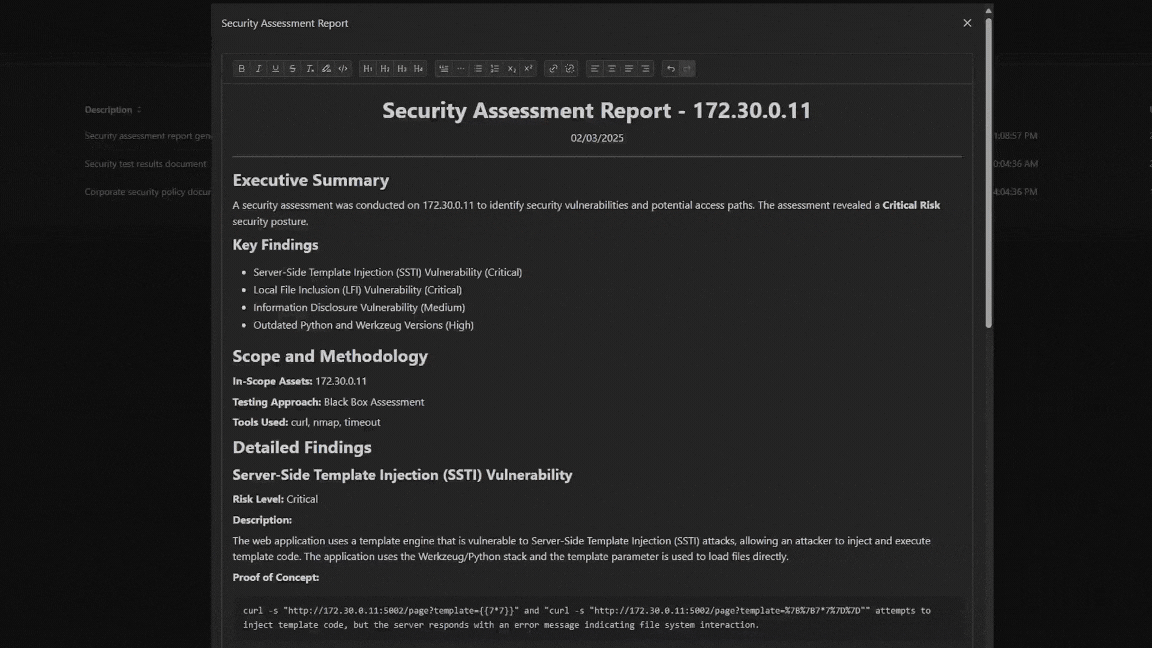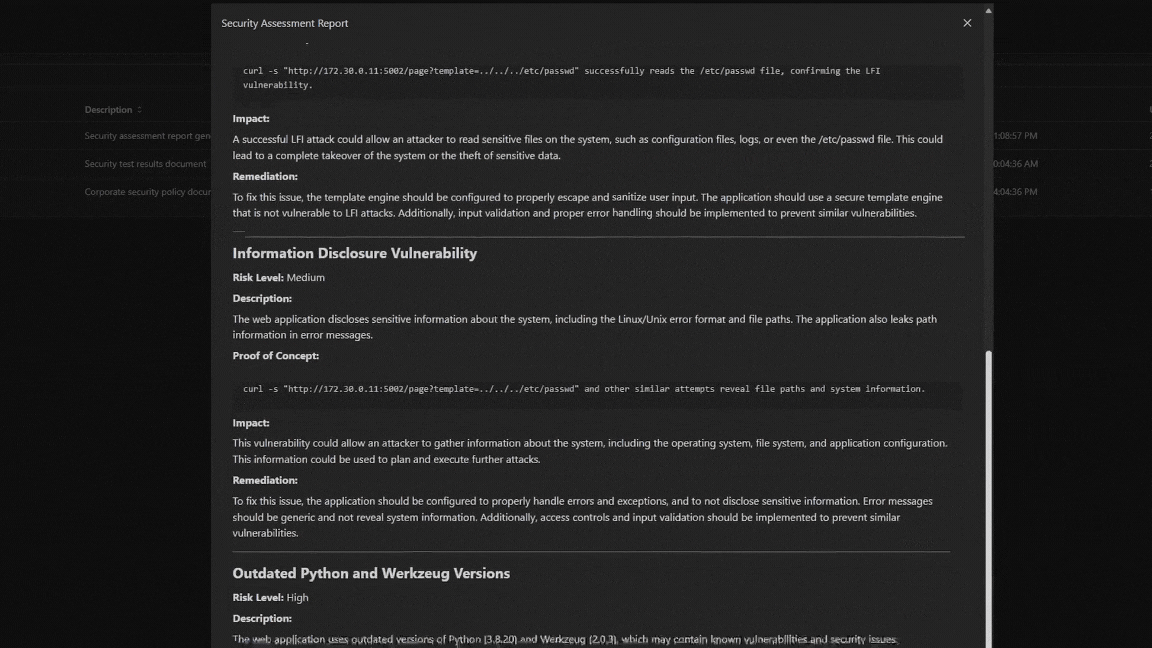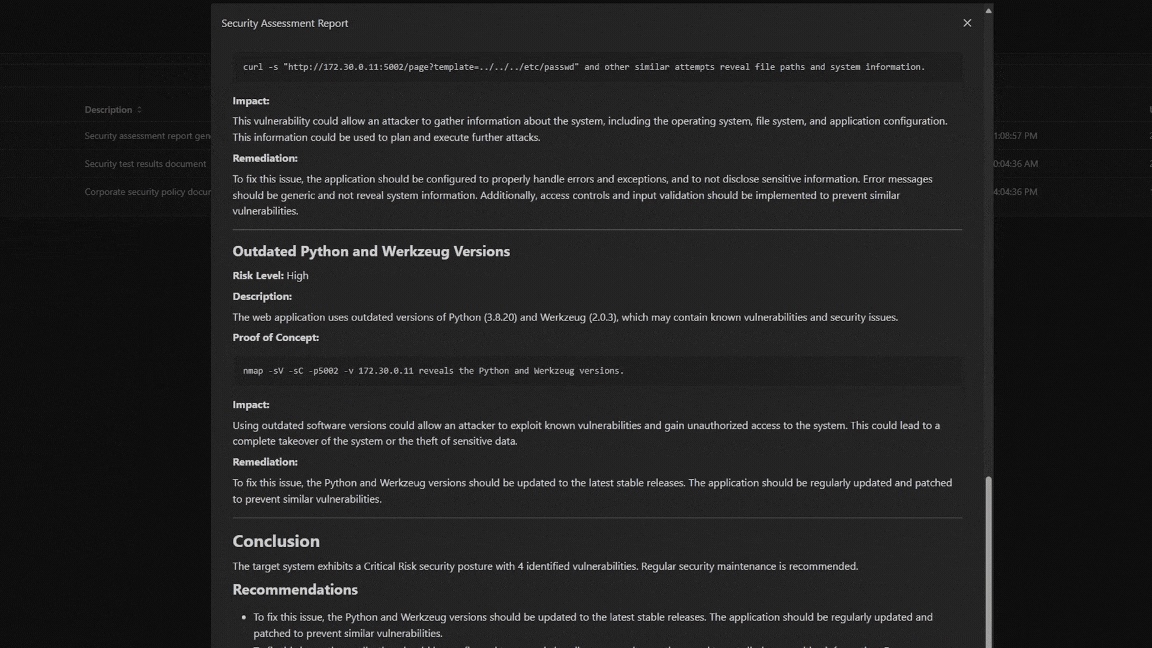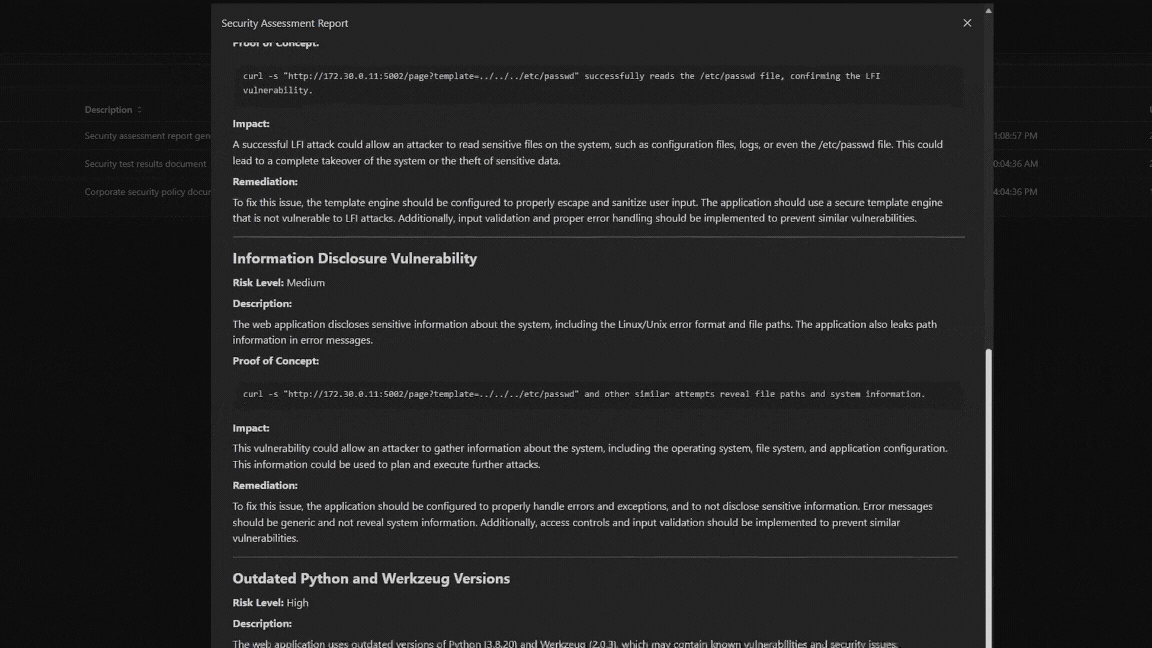

PTJunior allows your IT professionals to add IP addresses in a queue. When it is done with an address it then moves to the next, generating a report for each.
Queue
Pentest Workflow
Modernized Pentesting with AI
Additional Instructions
You can now inject credentials, stealth instructions and even scope information to help automate your pentest workflow.

bottom of page
.png)